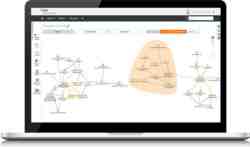
BMC Discovery e’ uno strumento estremamente efficiente, se non indispensabile, per condurre in maniera immediata ed aggiornata studi di Risk assessment (o risk analysis) e di business impact analysis
Mappa accuratamente le applicazioni e le connessioni in pochi minuti:
- Riduce le interruzioni del servizio grazie alla possibilità di prevedere e gestire i cambiamenti di configurazione.
- Effettua una mappatura completa delle informazioni software, hardware, di rete e di storage.
- Migliora i criteri di sicurezza con un inventario documentato al fine di soddisfare i requisiti di conformità.
- Dismette o consolida gli asset in modo riservato capendo le relazioni e l’impatto sul business.
La soluzione è agentless, infatti BMC Discovery è un’appliance virtuale pronta da usare. Il deploy richiede pochi minuti. Non c’è alcun processo di installazione, nessun database esterno da installare e configurare e nessun requisito di configurazione o di sistema operativo da rispettare.
Sotto il profilo della sicurezza, BMC Discovery utilizza standard di sicurezza certificati. L’applicazione virtuale infatti supporta FIPS 140-2 e rispetta NIST STIG.
Infine BMC Discovery si integra con qualunque CMDB oltre ad avere una integrazione nativa con il CMDB di BMC Remedy.
A corredo del pacchetto base sono disponibili due add-on opzionali:
- Extended Data Pack: che gestisce la end-of-life del supporto del software e dell’hardware al fine di evitare problemi di upgrade per software non più supportati o evitare inefficienze del hardware.
- Discovery for Storage: permette di includere nei processi ITSM componenenti storage di 25 brand diversi sia virtuali sia fisici. In questo modo il team di gestione può concentrarsi su una attività con connotati più strategici.